Authentication Services Market by Service (Compliance Management, Subscription Keys Management, Managed Public Key Infrastructure, and Reporting), Managed Authentication Type, Managed Tokenization Type, Vertical, and Region - Global Forecast to 2022
[118 Pages Report] The authentication services market is expected to grow from USD 507.0 Million in 2016 to USD 1,619.5 Million by 2022, at a Compound Annual Growth Rate (CAGR) of 21.1% during the forecast period. The scope of this research study covers the managed authentication services only. The base year considered for the study is 2016, and the forecast period is 2017–2022. Major drivers for the market is the growing number of digital identities and stringent data security regulations, such as PCI DSS and HIPAA.
Objectives of the Authentication Services Market Study
- To determine and forecast the global authentication services market by service types, managed authentication types, managed tokenization types, verticals, and regions from 2017 to 2022, and analyze various macro and microeconomic factors that affect the market growth
- To forecast the size of the market segments with respect to 5 main regions, namely, North America, Europe, Asia Pacific (APAC), Latin America, and Middle East and Africa (MEA)
- To provide detailed information regarding major factors (drivers, restraints, opportunities, and challenges) influencing the growth of the market
- To analyze each submarket with respect to individual growth trends, prospects, and contributions to the total market
- To analyze opportunities in the market for stakeholders by identifying high-growth segments of the market
- To profile the key market players, provide comparative analysis based on business overviews, regional presence, product offerings, business strategies, and key financials, and illustrate the competitive landscape of the market
- To track and analyze competitive developments, such as mergers and acquisitions, product developments, partnerships and collaborations, and Research and Development (R&D) activities in the market
The research methodology used to estimate and forecast the authentication services market begins with capturing data on key vendor revenues and the market size of individual segments through secondary sources, such as industry associations and trade journals. The vendor offerings are also taken into consideration to determine market segmentation. The bottom-up procedure was employed to arrive at the overall market size of the market from the individual services technology segment. After arriving at the overall market size, the total market was split into several segments and subsegments, which were then verified through primary research by conducting extensive interviews with key industry personnel, such as CEOs, VPs, directors, and executives. The data triangulation and market breakdown procedures were employed to complete the overall market engineering process and arrive at the exact statistics for all segments and subsegments.
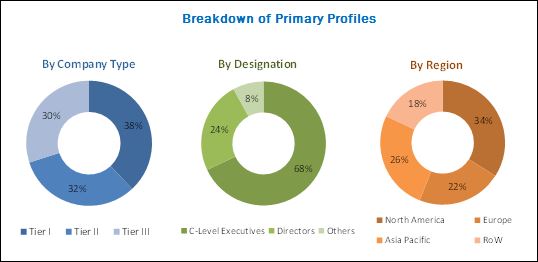
The breakdown of the profiles of the primary discussion participants is depicted in the figure below:
To know about the assumptions considered for the study, download the pdf brochure
The authentication services market ecosystem includes players, such as Verizon (US), Trustwave (US), Gemalto (the Netherlands), Wipro (India), Tata Communications (India), Bell Canada (Canada), GCI Channel Solutions (UK), Entrust Datacard (US), GCX (India), and Interoute (UK).
Key Target Audience for Authentication Services Market
- Management Security Service Providers (MSSPs)
- Cloud service providers
- Independent Software Vendors (ISVs)
- Information Technology (IT) companies
- Professional and managed service providers
- System integrators/migration service providers
- Managed authentication service providers
- Compliance management service providers
Scope of the Authentication Services Market
The report on the market takes into account several technology segments, deployment types, solutions, and services to arrive at the global market size for the market during the forecast period.
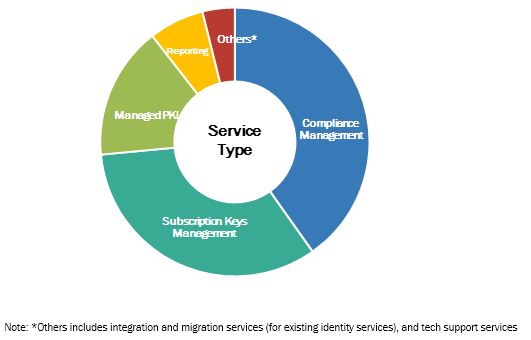
Authentication Services Market By Service
- Compliance Management
- Subscription Keys Management
- Managed Public Key Infrastructure (PKI)
- Reporting
- Others
By Managed Authentication Type
- Single-Factor Authentication
- Multi-Factor Authentication
By Managed Tokenization Type
- Token-based Authentication
- Tokenless Authentication
By Vertical
- Banking, Financial Services, and Insurance
- IT, ITES, and Telecom
- Government and Defense
- eCommerce
- Health Care
- Energy and Power
- Others (Media and Entertainment, Hospitality, Gaming, Education, and Manufacturing)
By Region
- North America
- Europe
- APAC
- MEA
- Latin America
Available Customizations
With the given market data, MarketsandMarkets offers customization as per the company’s specific requirements. The following customization options are available for the report:
Geographic Analysis
- Further country-level breakdown of the North American authentication services market
- Further country-level breakdown of the European market
- Further country-level breakdown of the APAC market
- Further country-level breakdown of the MEA market
- Further country-level breakdown of the Latin American market
Company Information
- Detailed analysis and profiling of additional market players
Government agencies pushing for standardization of data security protocols will drive the global authentication services market to USD 1.62 billion by 2022
Managed authentication services are the practice of protecting the enterprise and its assets from identity fraud and any other cyber threats that may hamper the stability of the business process. The managed authentication services use various authentication techniques to validate and authorize user credentials in real-time. Managed authentication services is a subsegment of Identity and Access Management (IAM). IAM can be described as the management of individual identities, their authorization, and provision of access based on predefined rules. Companies struggled to meet the compliance demands, resulting in deploying solutions limited to few applications and systems. In recent times, to mitigate these threats, companies are adopting managed authentication services, which helps in compliance management, password, and access authentication, synchronizing identities between directories, and providing access to sensitive enterprise applications and data on users’ preferred mobile devices. These services not only provide the highly secure environment, but they are economical, save time, and have high operational efficiency and management control.
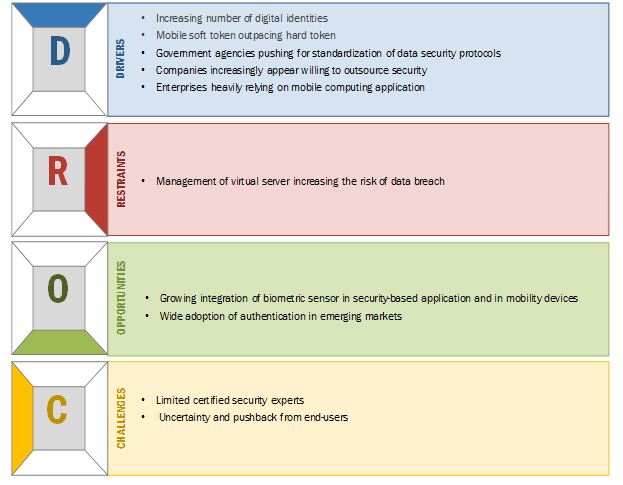
The major factors driving the growth of the managed authentication services market are increasing number of digital identities, rise of mobile and soft tokens, and the company’s willingness to outsource security. Managed authentication services offer measurable business value in terms of increasing revenue, increasing number of digital identities, mobile soft tokens outpacing hard tokens, government agencies pushing for standardization of data security protocols, companies increasingly willing to outsource security, and enterprises heavily relying on mobile computing application to provide remote access options to their employees and partners resulting in greater flexibility and ease of working. All these factors would greatly enhance the adoption of managed authentication services across various industry verticals, whereas, the growing integration of biometric sensor in security-based applications through smartphones, laptops, and tablets; the need for cloud-based authentication services; and wide adoption of authentication in emerging markets, provide enormous opportunities to the managed authentication services market.
Growing integration of biometric sensors in security-based application and in mobility devices and wide adoption of authentication services in emerging markets to provide the major opportunities in the market
Biometrics technologies used in device identification and access control and authorized human recognition with the use of human physiological or behavioural characteristics, such as iris, fingerprints, face, palm prints, retina, and voice. The technology behind biometrics has become cheaper and more reliable, and it has resulted in companies integrating various biometrics into their existing security system. Authentication service providers are continuously developing and innovating the biometric-based authentication. The best advantage of biometric technology is that the person need not remember any password or Personal Identification Number (PIN), as the biometric identity is unique for every human being in the world. Hence, it creates a big challenge for a cyber-attacker to breach it and offers numerous opportunity in various industry verticals. BFSI and eCommerce industry is expected to create huge opportunity for authentication service vendors to offer biometric-based authentication services to their clients for better security and data protection.
Authentication Services Market Dynamics
The authentication services market segmented by service, managed authentication type, managed tokenization type, vertical, and region. The managed PKI services is expected to hold the largest market share by growing at the highest CAGR during the forecast period. It is mainly due to an increasing need for managing and controlling large numbers of digital certificates for SSL, authentication, document signing, S/MIME, and other usages. Additionally, managed PKI services helps organization reduce the cost and burden of managing digital certificates.
The eCommerce segment is expected to grow at the highest CAGR during the forecast period. The eCommerce vertical deals with selling consumer products and services to its clients through multiple channels. eCommerce is one of the top cost-conscious verticals and the most targeted by cyber-attackers, because of the potential payouts and a large number of monetary transactions via credit and debit cards. In addition, the increasing complexities of supply chain, employees, channel partners, and customers are expected to be forcing etailers to adopt authentication services.
The Multi-Factor Authentication (MFA) segment is expected to hold the largest market share during the forecast period. Due to the increasing number of cyber-attacks and identity theft, organizations are implementing the two-factor authentication solution. The MFA adds an extra security layer and makes it more difficult for cyber criminals to breach an organization’s IT infrastructure. Additionally, various regulations and compliances, such as PCI DSS and GDPR, would drive the multifactor authentication segment’s growth.
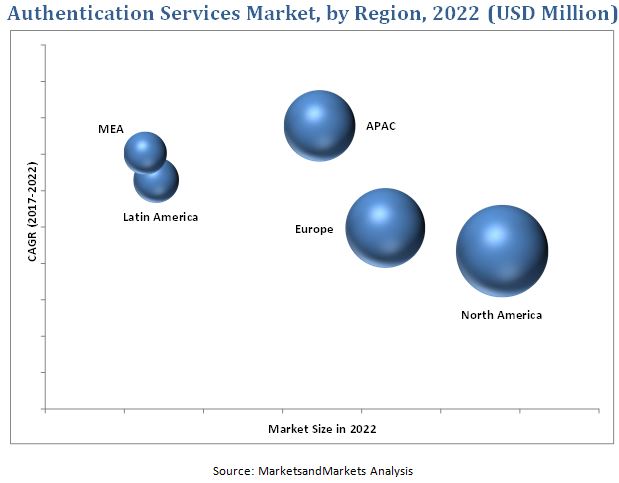
As per the geographic analysis, North America is expected to hold the largest market share during the forecast period. This is due to the presence of large managed security services providers, and stringent data security regulations and compliance in the region. The APAC region is expected to witness the fastest growth in the authentication services market, due to increaseing number of digital identities, online transactions, and mobile computing devices. Additionally, India, Japan, and Singapore have all updated or introduced new national cybersecurity policies that would ramp up the market.
The major restraining factor for the growth of authentication services market would be the management of virtual server that is increasing the risk of data breach, increasing response time in higher order authentication model, and the increasing cost and technical complexity in implementing the multi-factor authentication solution. Major vendors profiled in the report include Verizon (US), Trustwave (US), Gemalto (the Netherlands), Wipro (India), Tata Communications (India), Bell Canada (Canada), GCI Channel Solutions (UK), Entrust Datacard (US), GCX (India), and Interoute (UK).
The growth of authentication services market depends on the factors, such as Increasing number of digital identities, government agencies pushing for standardization of data security protocols, and enterprises heavily relying on mobile computing application.
Various established players and new entrants in the industry are offering authentication services solutions to meet the varying needs of the industry.
Compliance Management
Compliance management is one of the major elements of today's security administration. It offers clients an unmistakable way of building up consistency, preventing data leaks, and implementing relevant strategies. Compliance management allows enterprises’ teams to centrally monitor and manage the IT compliance obligations. It helps in streamlining the Governance, Risk, and Compliance (GRC) efforts and in establishing the business and technical requirements needed for an effective information security program.
Compliance management becomes even more crucial when the data or applications fall under Health Insurance Portability and Accountability Act (HIPAA), Sarbanes–Oxley Act (SOX), Family Educational Rights and Privacy Act (FERPA), PCI DSS, Gramm–Leach–Bliley Act (GLBA), or Basel compliance. For instance, PCI DSS is a standard developed by the credit card industry for ensuring the authentication of customers’ credit card information. The standard requires merchants and member service providers, who store, process, or transmit cardholder data, to build and maintain a secure IT network, protect cardholder data, maintain a vulnerability management program, implement strong access control measures, and regularly monitor and test networks. PCI DSS follows certain procedures to secure the credit card information that includes the installing of firewalls and anti-malware, and encrypting credit card data transmission. Hence, through compliance management services, organizations can adhere to and fulfil compliance requirement in an easy and cost-effective manner.
Subscription Keys Management
Subscription keys management helps in managing and securing an enterprise’s subscription keys that are required during the activation of enterprise software and applications. It enables organizations to track the subscription keys for any software or application that they have purchased. Subscription keys management offers fast, reliable, secure, and easy-to-use services for the protection of the users’ keys. It also enables the clients to efficiently store, backup, protect, and organize the encryption keys.
Managed Public Key Infrastructure
PKI enables organizations to manage large numbers of digital certificates for SSL, authentication, document signing, S/MIME, and other such usages of digital signatures. It helps in the secure transfer of data between the user and the server by authenticating the identity of the user. It encapsulates hardware, software, policies, and standards to manage the administration, distribution, and revocation of keys and digital certificates. An effective PKI consists of public key certificates, certificate repositories, certification authorities, registration authorities, and certificate management systems. Certificate authorities issue certificate and authenticate the identity of users, computers, and other computing devices. The KEY functions of the certificate authorities include generating key pairs, issuing digital certificates, publishing and verifying the certificates, and revocation of certificates. Registration authorities add an extra layer of security; they authenticate the person or company requesting the digital certificate to confirm their identity. Certificate management systems store and manage the issued certificates and certificate requests. Enterprises opt for managed PKI services, as they allow access to digital certificates without establishing, operating, and protecting the in-house certificate authority.
Reporting
Reporting is one of the important services that use the ready-to-use tool and service in generating and managing a report. It generates detailed logs about the user’s activity, which helps in security analysis and compliance auditing. A managed authentication report provides deep insights into the number of successful authentications, authentication activities, and the authentication methods used during a span of time. This reporting service comes with real-time fraud alerts. Whenever it detects a fraud activity, it sends alerts to the admin for locking out the user after a specified number of invalid logins. It also enables enterprises to mitigate risks by tracking the detailed logs and activities, and provides a complete list of the managed and unmanaged devices that connected to the enterprise applications.
Others
The other service types include integration and migration services (for existing identity services), and tech support services. The tech support services comprise the installation and ongoing support to help enterprises resolve frequent issues in their installed authentication services. Tech support services include 24/7 troubleshooting assistance, upgradation of the existing software, problem-solving, repairing, replacing failed components, proactive services, technical support by security experts, and test scenario management. Tech support services also include facility inspection and training, and round-the-clock support for the deployed authentication services. Integration and migration services help organizations in deploying and integrating new authentication services and migrating to new technologies as per their requirements and the systems’ compatibility.
Key questions
- What new opportunities are generated through ongoing government initiatives for security protocols?
- Which are the top use cases where authentication services can be implemented for revenue generation through IoT and cloud services?
- What potential opportunities have augmented due to increased outsourcing of security services, and how are managed authentication service providers getting benefitted from it?
- What should be your go-to-market strategy to expand the reach into developing countries across APAC, MEA, and Latin America?
To speak to our analyst for a discussion on the above findings, click Speak to Analyst
Table of Contents
1 Introduction (Page No. - 14)
1.1 Objectives of the Study
1.1.1 Business Intelligence
1.1.2 Competitive Intelligence
1.2 Market Definition
1.3 Market Scope
1.4 Years Considered for the Study
1.5 Currency
1.6 Stakeholders
2 Research Methodology (Page No. - 17)
2.1 Research Data
2.1.1 Breakdown of Primaries
2.1.2 Key Industry Insights
2.2 Market Size Estimation
2.3 Research Assumptions and Limitations
2.3.1 Assumptions
2.3.2 Limitations
3 Executive Summary (Page No. - 24)
4 Premium Insights (Page No. - 27)
4.1 Attractive Market Opportunities in the Global Market
4.2 Authentication Services Market By Service Type
4.3 Market Share Across Various Regions
4.4 Market By Authentication Type
4.5 Market By Tokenization Type
4.6 Market By Vertical
4.7 Market Investment Scenario
5 Managed Authentication Services Market Overview and Industry Trends (Page No. - 32)
5.1 Introduction
5.2 Managed Authentication Services: Technology Overview
5.3 Global Security Breach Snapshot
5.4 Use Case
5.5 Market Dynamics
5.5.1 Drivers
5.5.1.1 Increasing Number of Digital Identities
5.5.1.2 Mobile Soft Token Outpacing Hard Tokens
5.5.1.3 Government Agencies Pushing for Standardization of Data Security Protocols
5.5.1.4 Companies Increasingly Appear Willing to Outsource Security
5.5.1.5 Enterprises are Heavily Relying on Mobile Computing Application
5.5.2 Restraints
5.5.2.1 Management of Virtual Server Increasing the Risk of Data Breach
5.5.3 Opportunity
5.5.3.1 Growing Integration of Biometric Sensor in Security-Based Application and in Mobility Devices
5.5.3.2 Wide Adoption of Authentication in Emerging Markets
5.5.4 Challenges
5.5.4.1 Limited Certified Security Experts
5.5.4.2 Uncertainty and Pushback From End-User
5.6 Access Points
5.6.1 Endpoint Access
5.6.2 Local Access
5.6.3 Remote Access
6 Authentication Services Market By Authentication Type (Page No. - 41)
6.1 Introduction
6.2 Single-Factor Authentication
6.3 Multi-Factor Authentication
7 Market, By Tokenization Type (Page No. - 45)
7.1 Introduction
7.2 Token-Based Authentication
7.3 Tokenless Authentication
8 Market, By Service Type (Page No. - 49)
8.1 Introduction
8.2 Compliance Management
8.3 Subscription Keys Management
8.4 Managed Public Key Infrastructure
8.5 Reporting
8.6 Others
9 Managed Authentication Services Market By Vertical (Page No. - 56)
9.1 Introduction
9.2 Banking, Financial Services, and Insurance
9.3 Telecom, IT, and ITes
9.4 Government and Defense
9.5 Ecommerce
9.6 Healthcare
9.7 Energy and Power
9.8 Others
10 Market, By Region (Page No. - 65)
10.1 Introduction
10.2 North America
10.3 Europe
10.4 Asia Pacific
10.5 Middle East and Africa
10.6 Latin America
11 Competitive Landscape (Page No. - 81)
11.1 Overview
11.2 Competitive Scenario
11.2.1 New Service Launches
11.2.2 Expansions
11.2.3 Mergers and Acquisitions/Venture Funding
11.2.4 Agreements and Partnerships
12 Company Profiles (Page No. - 84)
(Business Overview, Services Offered, Recent Developments, MnM View, Key Strategies, SWOT Analysis)*
12.1 Introduction
12.2 Bell Canada
12.3 Gemalto
12.4 Tata Communications
12.5 Verizon
12.6 Wipro
12.7 Entrust Datacard
12.8 GCI Channel Solutions
12.9 GCX
12.10 Interoute
12.11 Trustwave
*Details on Business Overview, Services Offered, Recent Developments, MnM View, Key Strategies, SWOT Analysis Might Not Be Captured in Case of Unlisted Companies.
13 Appendix (Page No. - 109)
13.1 Key Industry Insights
13.2 Discussion Guide
13.3 Knowledge Store: Marketsandmarkets’ Subscription Portal
13.4 Introducing RT: Real-Time Market Intelligence
13.5 Available Customizations
13.6 Related Reports
13.7 Author Details
List of Tables (47 Tables)
Table 1 United States Dollar Exchange Rate, 2014–2017
Table 2 Authentication Services Market: Use Case
Table 3 Market Size By Authentication Type, 2015–2022 (USD Million)
Table 4 Authentication Type: Market Size By Region, 2015–2022 (USD Million)
Table 5 Single-Factor Authentication: Market Size By Region, 2015–2022 (USD Million)
Table 6 Multi-Factor Authentication: Market Size By Region, 2015–2022 (USD Million)
Table 7 Managed Authentication Services Market Size By Tokenization Type, 2015–2022 (USD Million)
Table 8 Tokenization Type: Market Size By Region, 2015–2022 (USD Million)
Table 9 Token-Based Authentication: Market Size By Region, 2015–2022 (USD Million)
Table 10 Tokenless Authentication: Market Size By Region, 2015–2022 (USD Million)
Table 11 Market Size, By Service Type, 2015–2022 (USD Million)
Table 12 Service Type: Market Size By Region, 2015–2022 (USD Million)
Table 13 Compliance Management: Market Size By Region, 2015–2022 (USD Million)
Table 14 Subscription Keys Management: Market Size By Region, 2015–2022 (USD Million)
Table 15 Managed Public Key Infrastructure: Market Size By Region, 2015–2022 (USD Million)
Table 16 Reporting: Market Size By Region, 2015–2022 (USD Million)
Table 17 Others: Market Size By Region, 2015–2022 (USD Million)
Table 18 Managed Authentication Services Market Size By Vertical, 2015–2022 (USD Million)
Table 19 Vertical: Market Size By Region, 2015–2022 (USD Million)
Table 20 Banking, Financial Services, and Insurance: Market Size By Region, 2015–2022 (USD Million)
Table 21 Telecom, IT, and ITes: Market Size By Region, 2015–2022 (USD Million)
Table 22 Government and Defense: Market Size By Region, 2015–2022 (USD Million)
Table 23 Ecommerce: Market Size By Region, 2015–2022 (USD Million)
Table 24 Healthcare: Market Size By Region, 2015–2022 (USD Million)
Table 25 Energy and Power: Market Size By Region, 2015–2022 (USD Million)
Table 26 Others: Market Size By Region, 2015–2022 (USD Million)
Table 27 Managed Authentication Services Market Size By Region, 2015–2022 (USD Million)
Table 28 North America: Market Size By Authentication Type, 2015–2022 (USD Million)
Table 29 North America: Market Size By Tokenization Type, 2015–2022 (USD Million)
Table 30 North America: Market Size By Service Type, 2015–2022 (USD Million)
Table 31 North America: Market Size By Vertical, 2015–2022 (USD Million)
Table 32 Europe: Market Size By Authentication Type, 2015–2022 (USD Million)
Table 33 Europe: Market Size By Tokenization Type, 2015–2022 (USD Million)
Table 34 Europe: Market Size By Service Type, 2015–2022 (USD Million)
Table 35 Europe: Market Size By Vertical, 2015–2022 (USD Million)
Table 36 Asia Pacific: Market Size, By Authentication Type, 2015–2022 (USD Million)
Table 37 Asia Pacific: Market Size By Tokenization Type, 2015–2022 (USD Million)
Table 38 Asia Pacific: Market Size By Service Type, 2015–2022 (USD Million)
Table 39 Asia Pacific: Market Size By Vertical, 2015–2022 (USD Million)
Table 40 Middle East and Africa: Market Size By Authentication Type, 2015–2022 (USD Million)
Table 41 Middle East and Africa: Managed Authentication Services Market Size, By Tokenization Type, 2015–2022 (USD Million)
Table 42 Middle East and Africa: Market Size By Service Type, 2015–2022 (USD Million)
Table 43 Middle East and Africa: Market Size By Vertical, 2015–2022 (USD Million)
Table 44 Latin America: Market Size By Authentication Type, 2015–2022 (USD Million)
Table 45 Latin America: Market Size By Tokenization Type, 2015–2022 (USD Million)
Table 46 Latin America: Market Size By Service Type, 2015–2022 (USD Million)
Table 47 Latin America: Market Size By Vertical, 2015–2022 (USD Million)
List of Figures (33 Figures)
Figure 1 Global Managed Authentication Services Market Segmentation
Figure 2 Global Market: Research Design
Figure 3 Research Methodology
Figure 4 Market Size Estimation Methodology: Bottom-Up Approach
Figure 5 Market Size Estimation Methodology: Top-Down Approach
Figure 6 Managed Authentication Services Market Analysis
Figure 7 Fastest Growing Segments in the Market
Figure 8 Increasing Number of Digital Identities is Expected to Drive the Market
Figure 9 Managed Public Key Infrastructure Segment is Expected to Hold the Largest Market Share During the Forecast Period.
Figure 10 North America is Estimated to Command Over the Market By Covering the Largest Market Size in 2017
Figure 11 Multi-Factor Authentication Segment is Expected to Hold the Larger Market Share By 2022
Figure 12 Tokenless Authentication Segment is Expected to Hold the Largest Market Share By 2022
Figure 13 Banking, Financial Services, and Insurance Vertical is Expected to Hold the Largest Market Share By 2022
Figure 14 Market Investment Scenario
Figure 15 Managed Authentication Services Market: Drivers, Restraints, Opportunities, and Challenges
Figure 16 The Multi-Factor Authentication Segment is Expected to Grow at A Higher CAGR During the Forecast Period
Figure 17 Tokenless Authentication Segment is Expected to Grow at A Higher CAGR During the Forecast Period
Figure 18 Managed Public Key Infrastructure Segment is Expected to Grow at the Highest CAGR During the Forecast Period
Figure 19 Ecommerce Vertical is Expected to Grow at the Highest CAGR During the Forecast Period
Figure 20 Asia Pacific is Expected to Grow at the Highest CAGR During the Forecast Period
Figure 21 Asia Pacific is Expected to Be A Hotspot for the Market During the Forecast Period
Figure 22 North America: Market Snapshot
Figure 23 Asia Pacific: Market Snapshot
Figure 24 Key Development By Leading Players in Managed Authentication Services Market for 2014–2017
Figure 25 Bell Canada: Company Snapshot
Figure 26 Bell Canada: SWOT Analysis
Figure 27 Gemalto: Company Snapshot
Figure 28 Gemalto: SWOT Analysis
Figure 29 Tata Communications: Company Snapshot
Figure 30 Tata Communications: SWOT Analysis
Figure 31 Verizon: SWOT Analysis
Figure 32 Wipro: Company Snapshot
Figure 33 Wipro: SWOT Analysis











Growth opportunities and latent adjacency in Authentication Services Market
Digital Identity; Identity Authentication; Digital Government; Digital Economy; Digital Transformation; PKI